This repository has been archived by the owner on Oct 6, 2019. It is now read-only.
-
Notifications
You must be signed in to change notification settings - Fork 167
Production Deployment
Tony Cai edited this page Aug 25, 2017
·
28 revisions
Steps:
- Write goldfish approle (only needs to be done once)
- Deploy goldfish binary
- Bootstrap goldfish with an approle secret id
This part only needs to be done once
# goldfish repo contains goldfish policy
git clone https://github.com/Caiyeon/goldfish.git
vault auth-enable approle
vault policy-write goldfish goldfish/vagrant/policies/goldfish.hcl
vault write auth/approle/role/goldfish role_name=goldfish policies=default,goldfish \
secret_id_num_uses=1 secret_id_ttl=5m period=24h token_ttl=0 token_max_ttl=0
vault write auth/approle/role/goldfish/role-id role_id=goldfish
# production goldfish needs a generic secret endpoint. See Configuration page for details
vault write secret/goldfish DefaultSecretPath="secret/" UserTransitKey="usertransit" BulletinPath="secret/bulletins/"
# [optional] to enable transit encryption:
# write key ServerTransitKey="goldfish" in the runtime settings (above)
# and run the following line to initialize the key:
vault write -f transit/keys/goldfish# on the host, disable swap for security
sudo swapoff -a
# IMPORTANT: don't forget to also disable ssh access!
# Download goldfish executable. Everything is packed inside.
GOLDFISH_VERSION=v0.7.0
curl -L -o goldfish https://github.com/Caiyeon/goldfish/releases/download/$GOLDFISH_VERSION/goldfish-linux-amd64
# provision a deployment config file (see repo config/sample.hcl for a full list of params)
cat <<EOF > config.hcl
listener "tcp" {
address = ":443" # listen on default https port
tls_cert_file = "path/to/cert"
tls_key_file = "path/to/key"
}
vault {
address = "https://vault.com:8200"
}
EOF
# launch the server (detached from shell by nohup) [Recommended: write as systemd service instead]
# sudo is required if you are using port 443
nohup sudo ./goldfish -config=config.hcl# generate a secret-id from approle. This MUST be wrapped!
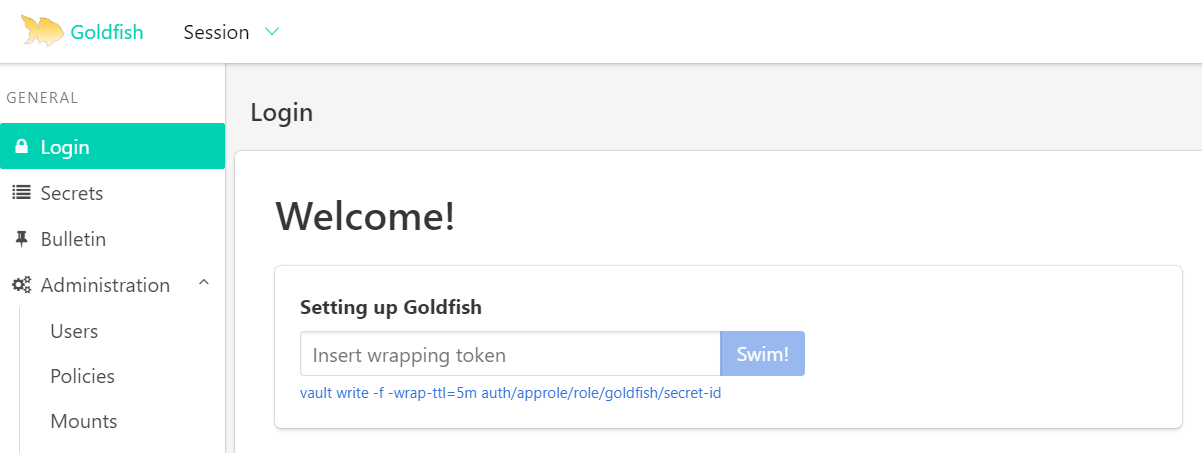
vault write -f -wrap-ttl=5m auth/approle/role/goldfish/secret-idHead to the login page of Goldfish. You should see this tile.
Insert the wrapping token to bootstrap goldfish. Upon success, goldfish is ready!
For more details on launch configurations, see here
For more details on run-time configurations, see here
For optional transit encryption and self-compiled goldfish, see here