Yet another set of CISSP mnemonics.
CISSP-mnemonics | CCSP-Mnemonics (for CISSP-passers)
the only mathematics in CISSP!
 |
 |
|---|---|
| (🍺) ALE causes AROSLE | (up my) SLEAV-EF |
| ALE = ARO x SLE | SLE = AV x EF |
🍺 = 😍 (get it?)
(up my) SLEAV-EF
-
SOX (Sarbanes Oxley, 2002) – [say in British accent] ENRON really SOX. Its transaction flow really SOX.
-
Gramm-Leach-Bliley Act (GLBA) – banks, lenders, insurance. Think about some fat banker Gramm (or Graham)
-
COPPA – Protects minors 13 or younger online. If you are an online pedo, then you cop it
-
FERPA – Protects Student data for over 18. Think about Phineas and FerP. They have to grow up eventually and go to college. It would be really unfortunate for Phineas and FerP fans if FerP's student card is leaked to public!
However, student ID leak won't trigger data breach laws. -
GISMA – Superseded by FISMA in 2000
-
FISMA – U.S. Government information security is under prisma. [NIST SP 800-53 is used for FISMA]
-
PCI DSS – Credit Card Security – Visa, MasterCard and American Express. What else is a card other than a credit card? – Your PCI card.
Note: PCI DSS is a Standard, not a law.
-
Digital Millenium Copyright Act (DMCA) – Copyright. Who hadn't heard of the DMCA strikes on Youtube?
-
4th Amendment in American Constitution grants right to privacy
-
Computer Fraud and Abuse Act – CFAA 1986 – First major legislation to fight cybercrime. Think: CFAA – F for First.
- Electronic Communications Privacy Act – ECPA 1986 – Makes it illegal to invade electronic privacy of an individual.
- Communication Assurance for Law Enforcement Act – CALEA 1994 – Amends ECPA to make wiretaps possible for law enforcement, regardless of technology used.
- USA PATRIOT Act of 2001 – Broadened wiretapping authorizations, no thanks to 9/11 in 2001.
Think of ECPA and CALEA – as a seed and a flower. Yes, calea is a plant, but let's make CALEA a CAULIPOWER with sour taste. ECPA grows into CALEA flower. Then terrorists come, and the garden of CALEA has to be destroyed. Like the privacy had to be destroyed.
- Export Administration Regulation (EAR) – restricting export of civilian items that may have military applications, such as EARphones.
- International Traffic in Arms Regulations (ITAR) – restricting export of war items. Think "ITAR is war". Russia has a century-old pro-war newsagency of ITAR-TASS, and when Russia started its full-scale war, U.S. already had Russia added to ITAR list.
- PII – Personal ID information
- PHI – Personal Health Information
- PCI – Credit card. PCI DSS applies
- HIPAA – Health privacy and security regulations in case you get HIPAAtitis. In HIPAA, BAA agreements are used to protect privacy.
- HITECH – Hospitals security go hi-tech!
- California Consumer Privacy Act – CCPA – in California only, require Privacy Statements from organizations. Similar mandatory effects to the EU's GDPR. Remember California=Privacy.
- HSA – Homeland Security Act. Creation of Homeland Security in the US. Mnemonic: "HSA is like HoUSA. HoUSA can be understood as "House" (my house is my castle) and "Home is USA". Related to HSA (2002) is USA PATRIOT Act of 2001.
- USPTO – Patents and Trademarks – (U.S. Patent & Trademark Office)
- LOC – Copyright – (Library of Congress)
- Bank – banking breach – (per PCI DSS)
- U.S. Code(x) – Criminal and Civil Law
- Code of Federal Regulations – Administrative Law on Federal scale
- Administrative – internal within organization, no set standard
- Civil – Civil litigation, preponderance of evidence standard
- Regulatory – Charges brought by regulatory bodies, substantial evidence standard
- Criminal – Charges by law enforcement, beyond the reasonable doubt standard
Risk = Threat x Vulnerability
- Inherent – Initial risk input before treatment
- Residual – Remaining risk residing after treatment
(No memory device here, more of an explanation)
- Qualitative – based on guestimates, inference and basic algorithms e.g., FAIR method (probability / impact) or ALE CAUSES AROSLE. Best for hard-to-quantify intangible assets.
- Quantitative – better, based on experience and statistics
- Combination – balanced
- Prepare.
- Categorize (systems)
- Select (controls) [for systems]
- Implement (controls) [+documentation]
- Assess (controls) [take a step back]
- Authorize (controls) [stamp of approval]
- Monitor.
PC SIA AM (PC of SIA in ArMenia)
For SIA to run a rogue PC in Armenia is pretty RISKy
PCS IAAM (PC-s I aam)
[Being non-human is RISKy]
DRP is a subset of BCP
- BCP – Business
- DRP – Technical
DC I DD PP
NSFL but rememberable memorization trick, oh boy will you need DRP and thus BCP after this
- Develop (policy)
- Conduct BIA (Business Impact Analysis)
- Identify (preventative controls)
- Develop DRP strategies
- Develop IT contingency (plan)
- Plan Training
- Plan maintenance
(No known memory device, just needs to be understood)
- Project Planning and Development
- Data collection
- Criticality Assessment
- Vulnerability assessment
-
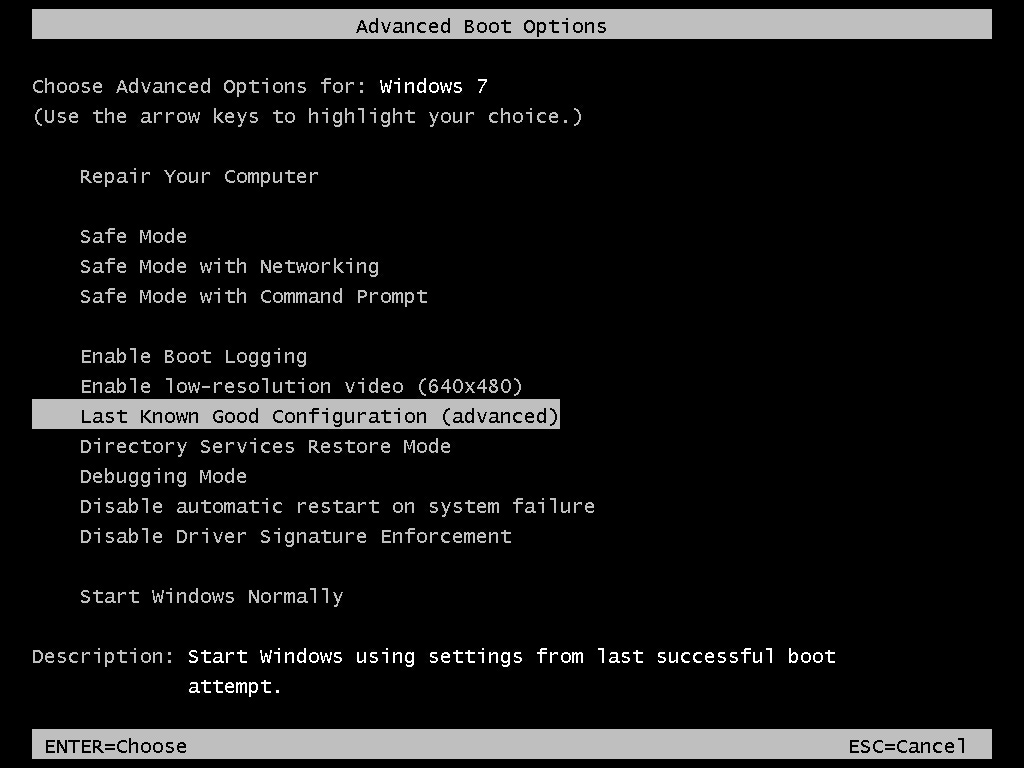
RPO – Recovery Point Objective – time period: From last (known good) scheduled backup to disaster (from past to present). Point – think about last known good configuration for Windows,
Last Known Good Point in time -
RTO – Recovery Time Objective – time period: from disaster to recovery, if all goes well (from present to the future).
-
WRT – How much work for technical staff to reconfigure everything after recovery.
-
MTD – Maximum tolerable downtime for business. For CISSP: MTD = RTO + WRT. In reality, YMMV.
-
Data Owner – (responsible) Overall
-
Data Processor – Processes Passed-on (database)
-
Data Custodian – (responsible for) Computer (with database)
-
Data Steward – (responsible for) Syndicate data everyday ["Syndicate" as in "Business", so responsible for business data.]
-
Administrators – Assign permissions to Accounts
- Data Controller – same as Data Owner
CISSPrep has a great mnemonic,
To memorize this, repeat the phrase “Cow, Pig, Sow,” or “CP SOW.” Repeat it again and think of a farm you visited or one that you saw in a movie. Now repeat the following mnemonic:
-
Clearing Can (be recovered)
-
Purging is Permanent
-
Sanitizing is the Same (as purging)
-
Overwriting with Oh's.
-
Wiping is Writing (overwriting, that is)
Notice how the letters match to help you remember. It seems silly, yes, but this is the key.
So here’s the phrase to keep repeating, once again:
Cow Pig Sow; CPSOW, Clearing Can, Purging is Permanent, Sanitizing Same, Overwriting Oh’s, Wiping is Writing. Repeat this over and over, and consider copying it onto a memorization sheet.
- Scoping – removing security controls that don't apply in your particular case.
- Tailoring – tweaking little details of applied security controls to better suit your organization.
- Supplementation – Specify used product names. For example, replace "OS" with "Windows".
There are two mnemonic devices.
Think about a digital telescope pointing at the stars.
- When you Scope, you zoom-in, and you no longer see stars you are not interested in
- When you Tailor, you tweak your zoom to see stars clearer
- When you Supplement, you take a photo of the galaxy, print it out, and then in the photo, circle and name each star with a pen.
- Scoping is Subtracting (controls)
- Tailoring is Tweaking (controls)
- Supplementing is Specifying (names)
(Zero) KODU – Kernel, OS, Drivers, Userspace
Total: 5 security models to know
- Memorization trick 1: Similarly categorizable models come one after another in alphabetical order!
- Memorization trick 2: Integrity models have I in it, Confidentiality models do not.
- Bell-LaPadula – (Confidentiality model) Like a BELL 🛎️: No Read Up↑, no Write Down↓.
Compiled: NoR↑🛎NoW↓. - Biba – (Integrity model) Opposite of Bell-LaPadula: No Read↓, no Write Up↑.
Compiled: NoR↓▽NoW↑.
-
Brewer&Nash: Think Chinese Brew tea – Chinese Wall. Walls off conflict-of-interest.
-
Clark-Wilson – (Integrity model) Use software to access data. Clerk uses WinStone software to access business data.
2 words, 4 commands.
- TAKE – Take someone else's permissions
- GRANT – Grant permissions to subordinates
- CREATE – Create new rule
- REMOVE – Remove a rule
- 23BRAIDS | DEREK | SHA HAVAL, MD (mirrored on archive.org / archive.vn )
- Information flow security models' properties (mirrored on archive.org / archive.vn )
- Dry pipe – Dry (steam)
- Wet pipe – Water
- Deluge – Deluxe (volume), once fire's detected
- Pre-action – preload once fire, action once confirmed
| Type | Application |
|---|---|
| A | Ash, almanac |
| B | Bubble, BOil Oil |
| C | Circuits, CRT |
| D | Dent, Dural, Duraluminium |
| K | Kitchen |
- Fault – short – (Technical) Faults don't last forever
- Blackout – (obviously) long
- Sag – short-term – sag even sounds short – sag sac
- Brownout – alike to blackout – long-term
- Spike – Spikes are momentary
- Surge – Like insurgencies, they can last long!
- Natural Access Control – Fences to enforce authZ
- Natural Surveillance – Remove trees so nobody can hide over trees
- Natural Territorial Reinforcement – Large windows to asset surveillance
What is not environmentally enforceable: AuthN.
- Magnetic – low security
- Proximity – signal can be stolen
- RFID – Distance
- Microchip / SmartCard – Secure
- Assurance – Assert (security of product)
- Certification – Compliance according to company's compliance security officer. Certification is towards assurance.
- Verification – Third-party observer's report. For example, when you register on a website, you "Verify your email" by receiving an email on a third-party email server (not blacklisted by the website admins).
- Validate – (drink valium to perform sanity check) [valium=diazepam]
- Accreditation – Ace's Compliance (senior manager)
- Acceptance – Accept
To remember IPSec, one needs to remember the following memory device: "IPSec is 2". What is 2?
-
2 of IPSec: IP + Sec
-
2 of Encapsulating Security Payload (ESP): Confidentiality + Integrity
-
2 of Authentication header (AH): "Authentication" + Integrity
From least secure to most secure:
Multilevel → Compartmented → System-High → Dedicated
M → C → S → D
Make up a story, e.g. "MC gives you a porn SD card.",
Progression of requirements for ALL information (therefore, next entry would apply for SOME information),
NDA → Clearance → Formal Approval → Need-to-know
NC→F→N -> NoiCy FaN [in the background]
Example: Compartmented – NDA for ALL info, Clearance for ALL information, Formal approval for SOME information, Need-to-know for some information.
-
Discretionary – Data owner discerns directly. [thus ACLs are in use]
-
Non-discretionary – everything more streamlined:
- Mandatory (MAC) – Military, and therefore strict and not scalable. Enforced by the OS. Clearances, formal approvals and need-to-know apply.
All other options are easier to remember,
- Attribute (ABAC) / Policy (PBAC) – attribute/policy – high-level rules, flexible use of attributes, location and environment.
- Role-based (RBAC) – role
- Rule-based (RuBAC) – rule – dumb rules for robots. example: firewalls
- Risk-based (
RiBACRBA, subtype of RuBAC) – risk. For example, IP from China increases risk score.
- Risk-based (
- ACLs – Access Control Lists. Blacklists or whitelists. Focus on Objects. Used in DAC.
- Capability table – Used for subjects in DAC.
sudoersfile is an example of Capability table. - AC Matrix – 2D matrix with subjects and objects in DAC/MAC.
- Lattice model – matrix of Labels on objects and subjects in MAC
- TCSEC – "Orange book" – US Standard
US Golden Gate Bridge is Orange (and TCSEC 'bridged' computing and security)
ITSEC – EU Standard
iT-Systems are European
Common Criteria – CC – Are superseding worldwide (commonly)
Start-from 1 – 3-2-1
FSM – SS – F
Function > Structure > Method >> Semiformal > Semiformal-verified >> Formal
An amazing mnemonic from CISSPrep,
The TCP/IP model on the right side can be memorized by saying/writing “N2, A3,” with “IT” in the middle, or “NitA”, which could be someone’s name.
NOTE: The mnemonic applies from bottom to top.
Taken from Reddit,
Some people F*** Bit**es
- Segments – TCP – Transport layer
- Packets – Netzwerking layer
- Frames – Data-link layer
- Bits – Physical layer
(typically)
- Kerberos – for Microsoft Windows
- RADIUS – for VPN
- TACACS+ – for Cisco
Mnemonic device – made up a little story: You send documents from Microsoft Windows via VPN to a mainframe serviced by Cisco. The corresponding authentication protocols would go in the alphabetical order.
Heads/Steps: Authentication (KDC), Authorization (TGS gives TGT Ticket), Acceptance
KATANA: KDC Authenticates, TGS Authorizes, nginx accepts. (You can use KATANA to chop off Kerberos's heads)
For CISSP: SSL is outdated and TLS is to be used.
VXLAN for LAN, SDWAN for WAN
For CISSP: VoIP doesn't mix well with VPN
- Distance-vector – Shortest distance
- Link-state – Best bandwidth link. Sophisticated. Network map is created.
NAC – Network Access Control
Note: They use Risk BAC, as they evaluate risk
- Pre-admit – Checks happen BEFORE admission
- Postadmission – Checks happen AFTER admission
- Client-based – Stateful
- Clientless – Stateless
Mnemonic device: They go in reserve alphabetical order
- Unicast – One
- Multicast – Many specific
- Broadcast – All
- P-AP (PAP), – Insecure, P for Pathetic
- CH-AP (CHAP) – Secure, uses CHecksums (hash functions)
- MS-CHAP – Microsoft-improved CHAP. Even more secure, uses CHecksums (hash functions)
- EAP – Original protocol that started its family. Outdated
- LEAP – Lightweight, Cisco proprietary, no longer secure
- PEAP – Protected EAP. For CISSP purposes, "good enough". Uses TLS.
- MS-PEAP – Microsoft's improvement on PEAP, even better than PEAP
- EAP-TLS – Secure, but difficult to implement due to additional prerequisites
- Bluejack – Jack sends annoying messages
- Bluesnarf – snatch data
- Bluebugging – bug to gain remote access
Bluetooth "authZ" is 4-digits.
- FCoE – Fiber and rarely Ethernet
- iSCSI – IP/Ethernet
- Class A: 10.0.0.0 – 10.255.255.255
- Class B: 172.16.0.0 – 172.31.255.255
- Class C: 192.168.0.0 – 192.168.255.255
Easy trick: class letter defines the number of 255's from left to right. For example, class B (2) would have 255.255.0.0
- Fraggle – CHARGEN
- Smurf – ICMP
Fragile CHARGE, Smurf Is CIMP:
Memory device – They are in alphabetic order,
- 20-21 – FTP
- 22 – SSH
- 23 – Telnet
Mnemonic device: This information is VERY obvious, so what do I say? Of Course! Or OFC:
- Open – Worst
- Filtered – OK
- Closed – Best
Quote from DerreckM/CISSP-Mnemonics (mirror)
-
Retinal scan is most intrusive to privacy (*think ret-inal = anal, intrusive! It's inappropriate, but you remember it!)
-
Using a condom is due care, taking the steps to decide whether to use the condom is due diligence. (Source: Luke Ahmed)
"Rejection" is a "positive" for authN systems.
- FRR – Type 1 Error
- FAR – Type 2 Error
- CER – Intersection between FAR and FRR. Optimal configuration.
Mnemonic device: FRR FAR, CER (meaning Freier's far, sire)
- Kerberos – symmetric AES encryption everywhere, but unique stateless system.
- RADIUS – UDP, can extraordinarily support TLS over TCP, only encrypts passwords. Like it is for VPNs, not a single sign-on
- TACACS+ – TCP, encrypts full session.
Think: Google, Github, Microsoft logon.
- OpenID – Identity → Authentication
- OAuth – (stands for) Open Authorization
Note: In real life, these protocols are used vis-a-vis.
- SAML – AuthN and AuthZ, open source, good for ADFS.
- SPML – Service Provisioning
- XACML – Access control (AuthZ but not AuthN)
- SOAP – messaging over network
- SCAP – Security Content (Automation Protocol) – Share threat intel
-
Permissions – for PC (for example, execute permissions on files in Linux)
-
Rights – for Real-life (for example, right to bear arms)
-
PRivileges = Permissions + Rights
Point is: Money, then assurance
Adapted from CISSPrep,
- SOC 1 – Finance First
- SOC 2 – Trust Second/Trust is Two
- SOC 3 – SOC 2 lite for public eyes.
- Type 1 – One point in time
- Type 2 – Two points – timeline
C in COBIT is always in place. COBIT – Common objectives for Common requirements for Computer systems. COBIT = Common
- Functional – use-cases/requirements
- Non-Functional – stability & performance
- Black-box – No knowledge
- White-box – All knowledge
- Gray-box – Black-box + SOME knowledge
- Static – Code [Static testing – is a subtype of white-box testing by definition]
- Dynamic – Runtime
- Unit – Automated
- Manual – Manual
- Use cases – How can it be used
- Misuse cases – How can it be misused
Wikipedia is wrong about this one (according to (ISC)² )
- Regression testing – Is there regression after the last change? Check for regression.
- Non-regression testing – Did last change have its supposed&intended improvement effect? Check for improvement.
- Authenticated – intranet
- Unauthenticated – externally facing targets only
- Test coverage – potential uses
- Code coverage – % of code executed in tests
- Function – functions work and return results
- Statement – line of code
- Condition – code executed under every input
- Branch – every IF-THEN-ELSE condition can be executed.
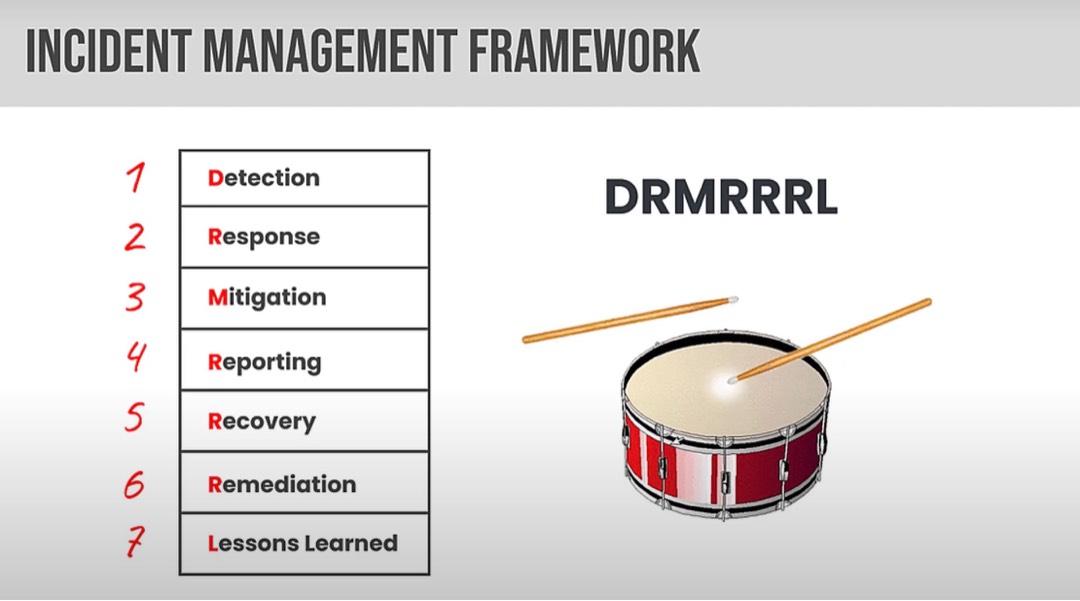 |
|---|
| DRM RRR L |
- Create
- Store
- Use
- Share
- Archive
- Destroy
- Letters: CS US AD
- Mnemonic: CompSci (of) US (created) ActiveDirectory
- Real – Real physical Objects
- Documentary – Docs
- Testimonial – Witness
- Primary – Originals
- Secondary – Certified copies
-
Hearsay – "he said she said" – bad
-
Direct – Very good
-
Corroborative – Supportive
-
Conclusive – so good, that we can adjourn court after it.
- Best – Original evidence is best (not photocopies)
- Parol – Written signed agreements can only be amended by written signed agreements (not parol evidence)
- Hearsay – Anti-hearsay evidence rule. Evidence-giver must present themselves and not through a third-party.
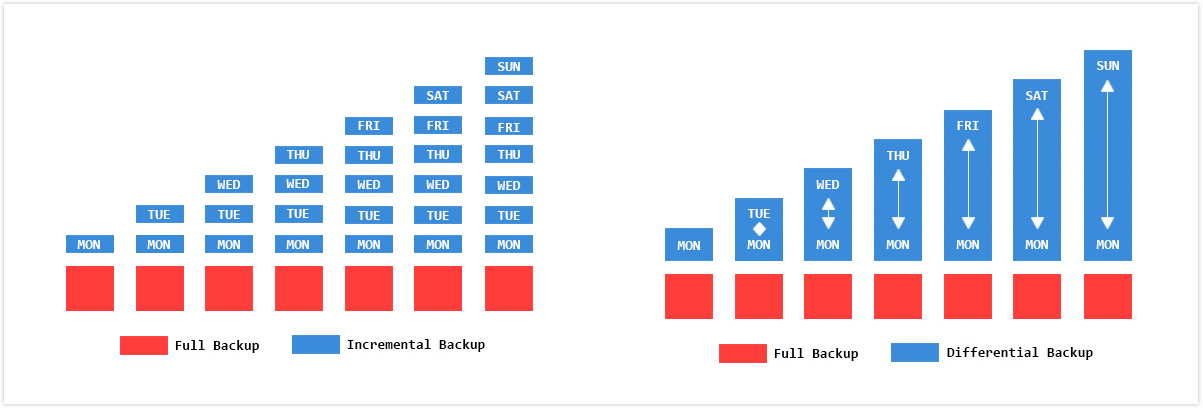
- Full – full
- Differential – diff (delta) from full
- Incremental – increments from last increment, thus there will be: high quantity of increments
- Security Event – Anything worthwhile logging for security. For example: OS reboot, browser crash
- Security Incident – Whatever breaches security policy and threatens organization
- Security Intrusion/Breach – Security defenses breached
- UCITA – Law governing business transactions
UEBA = Bossware.
Mnemonic: Associate "UEBA" with "Urban"
- Whichever boss uses UEBA is an
ueban(on UrbanDictionary)- UEBAn - can be thought as "urban cyberpunk" (cyberpunk surveillance)
HSM (Hierarchical Storage Management, not Hardware Security Module) – Move data from SSD to HDD or LTO to increase MTBF
- MTTF – Failure
- MTTR – Repair. Similar to WRT
- MTBF – Between failures. MTBF = MTTF + MTTR
Trick: to read from right to left,
- NAS – Storage in network
- SAN – Network of storages
- Striping – Speed
- Mirroring – Redundancy
Remember this array,
| 0 | 1 |
|---|---|
| S | M |
SM – Like "Samsung" or "storage management",
- RAID 0 – Striping – 2x speed
- RAID 1 – Mirroring – 2x redundancy
- RAID 2 – Byte striping for speed
- RAID 3 – Block striping for speed. Block is bigger than byte, therefore RAID 3 > RAID 2.
- RAID 5 – Data and parity striped
- RAID 6 – Same as RAID 5, but configuration is safer with little overhead over RAID 5
 |
|---|
| RAID 100 |
The trick is to read nested RAID from bottom to the top. First digit from the left defines the drive level,
-
RAID 01 – (At drive level) 0 Striping, (At drive-set level) 1 Mirroring
-
RAID 10 – (At drive level) 1 Mirroring, (At drive-set level) 0 Striping
Let's try one more for fun,
- RAID 100 – (At drive level) 1 Mirroring, (At drive-set level) 0 Striping, (At set of drive-sets level) 0 Striping
Trojan War gives a good analogy:
- Recon – Greeks analyze Trojan city, culture, forces to find vulnerabilities, and find that Trojans are superstitious.
- Weaponization – Greeks design and build an exploit – a Trojan Horse
- Delivery – Greeks discreetly deliver a Trojan Horse to the Trojan gates
- Installation – Trojan Horse is interacted with and installed inside Troy.
- Exploitation – Under the cover of the night, the Greek warriors disembark Trojan Horse and walk on small Trojan streets to avoid early detection.
- Command & Control – Greeks establish command and control over Troy
- Maintain – Greeks take measures to maintain control of the city as well as to seize the treasury of the previous king.
Recon weaponized, Delivery of exploit, exploit installed, Command and control maintained.
- (Change-)Request – User can request modifications
- Change (Control) – Developers can change what they do
- Change Advisory Board (CAB) – Approve/reject code changes
- Configuration – Comply with configuration policies
- Release – How software's released
User requests, developer changes, policy configures, software releases.
Ur DC PC SR
CISSPrep has a good mnemonic,
 |
|---|
| Please Fry Some Dead Animals To Catch The Right Man |
I segregate into: PFS-DA-TCT-RM
-
Agile – modern, agile dev philosophy. Effective, but not always best.
-
Lean – customer-first, Agile(-like) methodology, fermented by Toyota
-
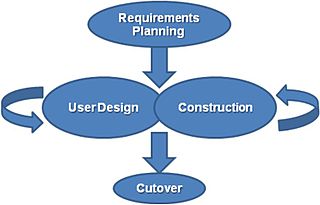
RAD – Rapid Application Development – Fast, iterative, less planning, adaptive 4 stages.
RAD -
JAD – Joint Application Development – RAD with more communication with stakeholders and advisors
-
-
Waterfall – Traditional. Best, if:
- Requirements are stringent
- Money isn't a problem
- Stable & secure (therefore quality) software is prioritized
- Spiral – Waterfall modification in spiral cycles.
- System Requirements (OS)
- Software Requirements (Software runs on an OS, so software requirements come second)
- Preliminary Design
- Detailed Design
- Code and Debug
- Testing
- Ops and Maintenance
2xRequirements, 2xDesign, Code+Testing, Maintenance
SoftWare Capability Maturity Model
Somewhat reminiscent of common criteria.
Mnemonic: IRDMO (THIRDMOON [of SW-CMM hell])
- Lvl 1: Initial: No plan
- Lvl 2: Repeatable: Basic lifecycle
- Lvl 3: Defined: Formal and documented DevOps
- Lvl 4: Managed: Quantitative measures (recall quantitative risk analysis)
- Lvl 5: Optimized: CI/CD
More hands-on
- Initiating (everything for DevOps)
- Diagnosing (what needs to be fixed/changed)
- Establishing (plan)
- Acting (on plan → DevOps)
- Learning (lessons)
- Dirty Read – Bad Reading timing
- Lost Update – Bad Writing Timing
- Incorrect Summary – Bad Summation Timing, see Tom Scott's video
- DDL – Data Definition language – Define (schema)
- DQL – Data Query Language – Query (data)
- DML – Data Manipulation Language – Manipulate (data)
- DCL – Data Control Language – Control (access). DCL sounds like ACL.
- TCL – Transaction Control Language – Transact
- Semantic – Strings mustn't be stored in integer fields
- Referential – Foreign keys correspond to corresponding primary keys
- Atomicity – Transactions are like binary atoms – either they happen fully, or don't happen at all.
- Isolation – Transactions are isolated from one another
- Consistency – Transactions consistently obey integrity rules
- Durability – Transactions can always be restored to safe-state (with DuraCELL batteries)
- Aggregation – Aggressively collect non-sensitive information to compile sensitive information
- Inference – Infer from non-sensitive information + a guess
-
Knowledge systems – Inference (like qualitative risk analysis). Types,
- Forward – From Known-inputs to Goal
- Backward – From Goal to Known-inputs
-
Machine learning (ML) – Basic algorithms
-
Neural networks – Like human brain
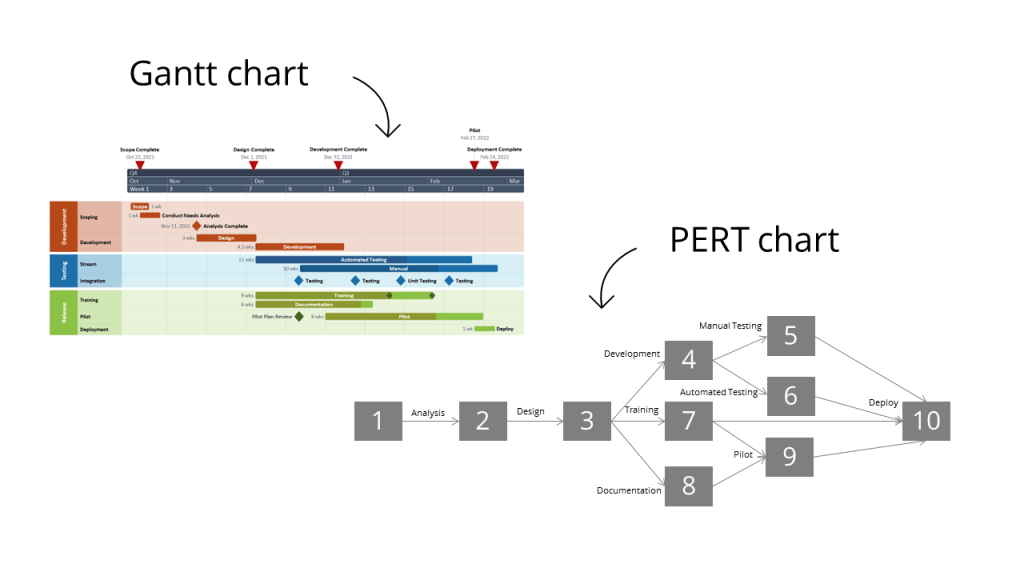
- Gantt chart – like timelines on Wikipedia, (example).
- PERT Chart – Project management modelling graph, (example).
No source is perfect, including this one. Everyone makes mistakes, and I witnessed several contradicting opinions online about some hot topics (especially about Access Control Models, due diligence vs due care, DR). The trick is to consult multiple sources.
This set of mnemonics, like any other set, probably only covers 40% of all exam topics. For the remainder 60%, you need to study books. The mnemonics are a result of thorough studies, not a replacement of studies.
Also, try to make multiple mental connections to the CISSP topics. Through experience, language (like "Zero KODU"), cursing etc. Don't be that guy, who passed CISSP and forgot what Bell-LaPadula is. During the exam, it's one too easy not to remember something, and I could answer some of the hard questions through thoroughly mentally consulting the topics I studied.
For CISSP, the right way is (ISC)² way (and to give credit, they are at least almost always right).
CISSP mnemonics do not, and cannot, replace going through all CISSP topics.
I recommend,
- Official (ISC)² CISSP publications
- Read questions multiple times, to decipher what is being asked.
- If an issue affects both confidentiality and integrity – then it mainly affects confidentiality.
- If an issue affects Least Privilege and Separation of Duties – then it mainly affects Separation of Duties.
- Think like a technical manager – not a senior techie.
- Order of criticality: Humans > Laws&Regulations > Company > Computer hardware
- External opinion about security is always more objective than internal.
- End game matters. Yes, you have an 'amazing' trick to keep your organization secure. Will it still function as expected in 5-10 years?
- Protect society, the common good, necessary public trust and confidence, and the infrastructure.
- Act honorably, honestly, justly, responsibly, and legally.
- Provide diligent and competent service to principals.
- Advance and protect the profession.
- Protect (commonwealth)
- Act (well)
- Provide (service)
- Advance (profession)
P-A-P-A
The descriptions get shorter every time
Story of a "PAPA" man following Code
(icons from Iconfinder, used for educational purposes)