-
Notifications
You must be signed in to change notification settings - Fork 963
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
"De novo" project creation via API tokens/OIDC #11296
Comments
|
From discussions, I'm currently leaning towards solution (1). Here's the proposed flow:
Additional considerations:
|
|
Working on this this week. |
|
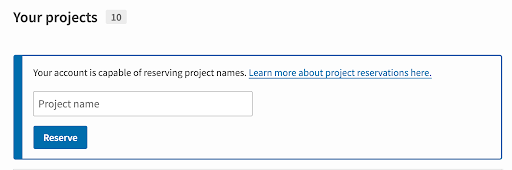
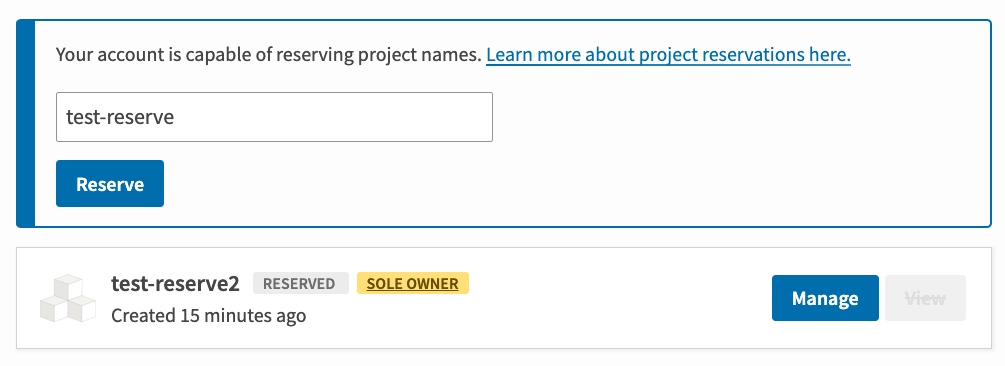
Just some notes: We'll probably want the button for this under the project management view ( ...probably right below "Your projects," with language like "Reserve a project name." The button will be inactive if the user isn't eligible to reserve a project name (per the restrictions above). Clicking that button should, in turn, produce a form modal (not a separate page, since it's pretty much a single input) that includes (1) the name to reserve, and (2) a confirmation checkbox ("I understand that this is a temporary reservation, and that I need to upload a package in the next XX hours to make it permanent"), plus a submit button. Pressing the button should produce a success or error flash, as appropriate. |
|
Hi @woodruffw, it's great that this effort is getting revived. Have you seen the previous discussion and my previous suggestions @ #6378 (comment) + #6378 (comment). It seems that people in the discussion agreed that it was a good idea, and it seems to partially align with what you're describing here. So I'm mostly just checking to see if you know about it and whether you're planning to incorporate those ideas. |
|
I did, thanks! And thanks for cross-referencing as well. I think the ultimate plan here is close to what you commented in that issue: we aren't planning single-use tokens, and instead we're going to make "reservations" part of the Warehouse UI. I'll have some initial work pushed up soon to demonstrate the rough idea there. |
|
@woodruffw that sounds roughly what I had in mind originally (except for the expiration part). Do you think the |
|
I think we want to limit this to use by OIDC publishers only (see #11272). |
I might not be understanding, but I think there's a chicken-and-egg problem with restricting this to OIDC publishers: we don't know which publishers have been registered against with PyPI projects until the project already exists, so we can't temporarily register the project itself via OIDC. The exception to that would be some kind of "TOFU" scheme, where the user could submit their OIDC token to an endpoint with the project name they'd like to reserve, which would then reserve it and produce a scoped API token. I think that would work, but it would need to be slightly different than the endpoint we've already built in #11272 (since it would need to specify the project being created). But even then we'd need to figure out how to add the owner role to the temporary project, since we don't know (ahead of time) which PyPI users are associated with which OIDC publishers. |
|
I'm thinking that there would be an 'add a publisher' view that has a free-form field for the project name, limited to projects that don't exist -- so The user creates the publisher, which doesn't necessarily reserve the project name, but lives in a 'pending' state until it enables them to publish successfully, creating a strong relationship between the As a result, we don't need 'reservations' or expirations, because if another user (or publisher) successfully publishes it before they do, we can just deactivate/disable all other publishers that are in a 'pending' state for that project name. So, sort of TOFU, but more like TOFU with a headsup? |
|
I think that scheme makes sense! I'll need to think some more about how to shoehorn this into the existing Some things I'm not sure about yet:
Some random ideas (not fully fleshed out):
|
I think they should both be honored? This wouldn't be any different than setting the same publisher for multiple existing projects now.
This should be the user that created the publisher -- probably something we want to track anyways.
I think either approach could work. The |
Makes sense! Yeah, we should definitely be tracking this.
Yeah, I think I'm leaning towards the |
|
Now that the initial models are merged, I'm going to start work on the corresponding routes and views. My current plan: a new "Publishing" link under the "Your account" ToC, which goes to a new view just for pending OIDC publishers. This view will closely mirror the extant Edit: Something like this: |
|
Just to fully enumerate the behavior here, this is how API token exchange with a "pending" OIDC provider will work:
Then, if the pending provider's project does not already exist, it is created, a temporary macaroon is minted for it, and the If the pending provider's project does already exist, then the |
|
From discussion with @di, there are some additional constraints we'll need to impose to limit the potential for abuse from "pending" OIDC providers:
Finally: we should not give pending OIDC providers an expiration window: doing so would would allow an attacker to place a reservation as soon as the legitimate user's reservation has expired, leading to a confusing situation where the legitimate user believes they're creating a project under their own account but are actually creating it under the attacker's account. Edit: With these constraints, the Edit: These constraints have been added to #12646. |
|
#12646 is the the penultimate component of this: it adds the views, routes, forms, etc. needed to register and manage "pending" OIDC providers. I'll do a follow-up PR for the final part, which will be validating OIDC JWTs using those "pending" providers similarly to the current functionality for "normal" OIDC providers. |
|
I'll open the final PR to close this out after #12646 is merged. Here's an enumeration of its behavior when
|
|
Oh, and some miscellaneous cleanup/usability tasks:
|
This should probably just happen at upload time, when the project is created by the unrelated third party (and we should probably notify the owner of the pending provider) |
Makes sense! |
What about non-OIDC publishers? I think, it'd make sense to still support my original idea for those. Probably as a disconnected effort, though. |
|
Status update: starting work on those follow-on items now. |
|
@woodruffw when will this be available for early testing? I'd like to try it out and I hope to introduce it into the pypi-publish GitHub Action too. |


There's currently a little bit of friction around bootstrapping API tokens on a new PyPI project:
A similar problem will happen with OIDC: we currently require a project to exist before an OIDC publisher can be registered against it, meaning that a user will have to upload at least one release with a user-scoped token or credentials before they can switch to a credential-less workflow.
Some potential solutions:
The text was updated successfully, but these errors were encountered: