-
Notifications
You must be signed in to change notification settings - Fork 29.6k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
meta: semver impact of Error messages #13937
Comments
|
Since this is tagged I don’t have a strong personal opinion about this, but I see @mscdex’ point, and I would be okay with considering these semver-major while Node 8 is Current (but trying to clearly message that that is going to change with the next major version). |
|
Generally I don't see the point in pushing it out further like that. Switching to the new mechanism is already semver-major which means the overwhelming majority of changes in this area already won't be in 8.x at any point in time. Those that are in 8.x were also semver-major changes that users will already be adapting to -- which involves moving away from checking the error message text in favor of checking the code. Requiring that these all be semver-major while 8.x is current won't provide any tangible benefit. |
|
Should this be put on the LTS WG agenda? I'm OK with LTS being the final arbiter on what is and isn't a breaking change. (And if that isn't written into their charter, perhaps it ought to be?) |
|
(Might also be good to clarify if LTS WG is the small-ish number of people listed in the LTS repo README or the considerably larger group of people on the @nodejs/lts team.) |
|
|
I'd like to see a citgm run - I think we can actually test if this must be semver major or not relatively quickly. I'm not sure on what PR I should run the citgm run against though - would love assistance with that. |
IMHO this is one of those things where end user code could be just as easily affected as modules on npm. |
|
@mscdex my point was that if CITGM is red (and it is red) we have to mark it semver-major (and we should). Since it breaks stuff in the ecosystem we can be sure it breaks user code. We should also probably notify those 50 packages in NPM about the breakage. |
|
I'm thinking we need a communications push along with some period of time for people to adjust. Ideally we'd have all of the messages moved over and then do a fair bit of communications/evangelism. Its going to be easier to say it applies to all messages than explaining a different policy based on the message. For messages that we have moved over (semver-major) and are changing again the main question to me is if there has been enough communication/knowledge transfer so that developers know that they should no longer be checking the error message and instead use the error code so that they don't get affected by the second change. Until then I was thinking it would be safer to continue to mark them as semver-major. |
|
@mhdawson it will take some time. Module author needs to adjust, and old versions of Node.js phase out. I would say we should wait until Node 10 goes LTS, i.e. we might stop considering these changed after 2 current releases (one of which LTS) with the new system. |
|
So anyway I marked #13730 that's already in master |
|
@mcollina I agree it might take some time. I don't think we need to decide when we might be ready, but we do want agreement on whether we are not ready yet and should continue to mark them SemVer major for now. |
|
@nodejs/ctc do we want to talk about this in the next meeting? |
|
I've tagged with ctc-agenda |
|
@nodejs/ctc Currently, this is the only issue for the meeting this week. If I'm understanding everyone's text and GitHub reaction emoji things correctly, expressed opinions thus far are: CTC folks
Other Collaborators and Contributors
Anyone else care to weigh in? @nodejs/collaborators As of now, we don't have consensus and I don't think we are likely to get consensus before the meeting. If I had to guess, I'd say this is going to end up going to a CTC vote. I'd therefore ask that @nodejs/ctc members decide that either they are OK with any result or else invest whatever time is needed to come to an opinion before the meeting this week. Of course, you may change your mind during the meeting based on conversation etc. But if it comes to a vote, I would prefer we actually have resolution on the vote quickly. |
|
My opinion: While I really want message changes to not be semver-major anymore, the fact is our own docs say:
True, it says in the "Using Internal Errors" guide that "once using internal/errors, changes to internal/errors error messages will be handled as semver-minor or semver-patch." However, by definition, guides are more advisory and less binding than other docs. (I know that I certainly review all CTC governance doc changes very closely while I tend to be less granular in my reviews for guides unless the guide happens to be on a topic I am extremely interested in. And I suspect I'm not the only person for whom that's true.) When a guide contradicts our governance docs or other docs, the contradictory element of the guide should be disregarded at least until the docs are updated. (I'm using "should" and not "must" very deliberately in that previous sentence.) There is clearly at least a "remote chance of breaking something" with message changes. That's why we're having this conversation. Therefore, these sorts of changes should be treated as semver-major at the current time. Response to some obvious objections:
|
|
I had an idea for a middle ground solution. Declare that the move to the new Errors and their messages are experimental for the pre-v9.0 timeframe, and changes carry a blanket do-not-land-on-*. |
Has getting sufficient CTC approval on message changes been a significant problem? (Honest question. I don't know the answer.) |
A bit. |
|
@refack Thanks for compiling that list. A few things: Correction: That PR itself has only been open for 12 days and had two CTC approvals after 9 days. More importantly, two things: First, I was asking specifically about PRs for message changes. Most of these are about initial implementation of the internal errors stuff so will be subject to the two-CTC-approvals rule no matter what we decide on this issue. Simple message changes should be easy to review and thus likely incur a smaller cost in terms of delay waiting for two CTC approvals. Second, I think the useful metric here is the time difference between when a PR could have landed if it wasn't semver-major vs. how long it took as a semver-major. So let's remove the ones that were about more than straightforward changing the text of an error message or two. We're left with only one PR from that list:
That said, that is only one data point and I wouldn't want to draw too sweeping a conclusion (or, really, any conclusion) from it. I'd say at this point that we don't really know if keeping message changes as semver major is going to greatly delay PRs from landing. Probably the right place to look for more data (if anyone is so inclined!) would be message changes on old-style errors. There is unanimity that those should be semver-major so that will tell us what the cost is rather than incorporate the cost of uncertainty and in-tracker debate about it. |
My experience maintaining a module across a wide range of Node.js versions is that it gets extremely complicated over time as core move faster than the community. Look at the rig we have to maintain to make If that initiative starts, I think both myself and @calvinmetcalf should be on the team, as we might need something clever there to support streams. |
Not so ASAP since we didn't finish mapping all the errors 😞. But otherwise sounds like a great idea. |
|
At the CTC meeting today, consensus was these message changes are still The issue of difficulty getting two CTC approvals came up and there was some discussion around how we might address that. /cc @MylesBorins @jasnell |
|
CTC (and this thread)'s decision: |
|
If landing time will be an issue I'll open a new thread. |
One thing to note: once we declare that policy (which we in fact did here), changing that policy itself would be a |
|
Was there any discussion of my suggestion for a cross-node core-included error code package? |
@ljharb No. TBH I encouraged us to make a decision on whether these are breaking changes, and to discuss other issues (2-CTC approval issues, how to get the new errors implemented faster, etc.) in GitHub issues. |
|
@ljharb I believe @jasnell talked about making the internal error system an npm package that readable-stream can depend on? EDIT: oh I see it is already mentioned in #13937 (comment), it currently needs a bit of work to work on older versions of node. |
AFAICT That's orthogonal. Maybe if it's up and running and adopted, we could trigger a reevaluation of the severity policy. P.S. I have been thinking of way to assemble a map of error messages to error code, efficiently, and across release line... Not so trivial 🤔 |
PR-URL: nodejs#14375 Refs: nodejs#13937 Reviewed-By: Anna Henningsen <[email protected]> Reviewed-By: Rich Trott <[email protected]> Reviewed-By: Luigi Pinca <[email protected]> Reviewed-By: Timothy Gu <[email protected]> Reviewed-By: Colin Ihrig <[email protected]> Reviewed-By: Tobias Nießen <[email protected]> Reviewed-By: James M Snell <[email protected]> Reviewed-By: Matteo Collina <[email protected]>
PR-URL: #14375 Refs: #13937 Reviewed-By: Anna Henningsen <[email protected]> Reviewed-By: Rich Trott <[email protected]> Reviewed-By: Luigi Pinca <[email protected]> Reviewed-By: Timothy Gu <[email protected]> Reviewed-By: Colin Ihrig <[email protected]> Reviewed-By: Tobias Nießen <[email protected]> Reviewed-By: James M Snell <[email protected]> Reviewed-By: Matteo Collina <[email protected]>
PR-URL: #14375 Refs: #13937 Reviewed-By: Anna Henningsen <[email protected]> Reviewed-By: Rich Trott <[email protected]> Reviewed-By: Luigi Pinca <[email protected]> Reviewed-By: Timothy Gu <[email protected]> Reviewed-By: Colin Ihrig <[email protected]> Reviewed-By: Tobias Nießen <[email protected]> Reviewed-By: James M Snell <[email protected]> Reviewed-By: Matteo Collina <[email protected]>
|
I read in this article https://medium.com/the-node-js-collection/node-js-errors-changes-you-need-to-know-about-dc8c82417f65 that there is a plan to change the
|
@jondubois valid comment, so just to be clear this change will only affect Errors that dgram.createSocket('i like rabbits')core would throw new Error('Bad socket type specified. Valid types are: udp4, udp6');now instead the Error will have a {
code: 'ERR_SOCKET_BAD_TYPE',
type: Error,
message: /^Bad socket type specified\. Valid types are: udp4, udp6$/
name: `Error [ERR_SOCKET_BAD_TYPE]`
} |
|
I agree that adding the code to the Personally I see
Checking I would prefer if both |
Please, allow us to set throw new Error("Message", "ERR_CODE"); |
|
@haykam821 that's part of the JS language itself, and is not something node should do. You can do |
|
@ljharb Yes |
|
Though, Node can (and in my opinion - should) expose helper function for creating errors with code. |
|
Eventually, perhaps. For now the focus is on making sure all of node.js' own errors have assigned codes and consistent error messages |
masterContext
There is an ongoing effort to migrate all JS expectations throws by
nodecore to have a.codeproperty. The error code allows userland to react in different exceptions specific ways.To that extent a new internal module (
internal/errors) was created #11220 and the migration is tracked in #11273 (and to less extent in https://github.com/nodejs/node/projects/4) Some module migrations landed in[email protected], some have landed inmastersince, and some have yet to be migrated. Hence it can't be asserted thatnodecore will only throw errors with an error-code, and so we have to assume the existence of userland code that depends onerror.messageparsing.Issue
At present there seems to be a difference of opinions as to the semver level of changes in messages of
internal/errors.Action item
A consensus should be reached on this issue as we want to have a clear path forward, and unambiguous guidelines for contributors.
Relevant discussion
guides/using-internal-errors.mdinternal/errors: improve ERR_INVALID_ARG_TYPE #13730 (comment)

internal/errors: improve ERR_INVALID_ARG_TYPE #13730 (comment) (landed as

semver-patchbut markeddon't land on v8.xuntil discoution is concluded)errors: improve invalid arg type #13834 (comment)
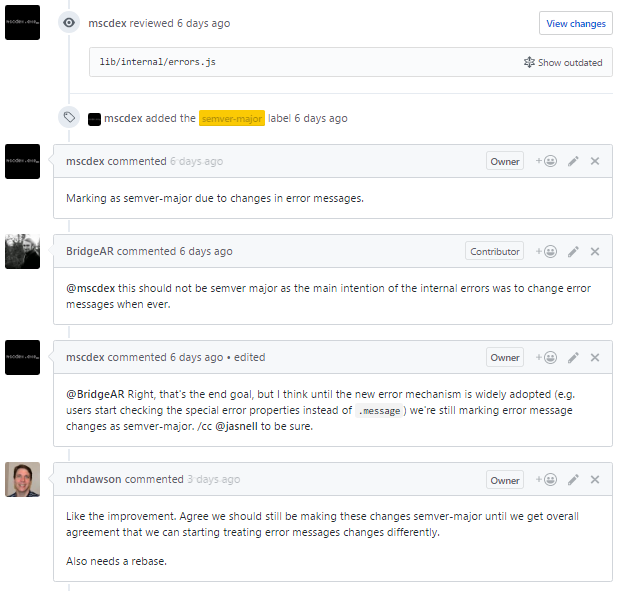
[EDIT by @Trott:
don't land->don't land on v8.xfor clarity.]The text was updated successfully, but these errors were encountered: